“A 2010 study by Google found in excess of 11,000 domains hosting fake anti-virus software, accounting for 50% of all malware delivered via internet advertising.”
The Fake Antivirus Software or Fake Virus Detection Software Scams
If you go anywhere on the Internet, you are bound to run across one of the most insidious scams happening today: Fake Virus Detection software. The worst feature of this scam is that it tricks users into believing they have an infection on their machine and offers a way to clear it. Eventually getting hit by one of these is bound to happen. Both experienced as well as novice computer users are subject to these. Most often, the only indication that something is wrong might be a strange ad window that keeps automatically popping up whenever you’re browsing the Internet. Or, your computer slows down to an annoying crawl. Many people who are faced with these issues just turn to the Internet for either free or paid antivirus software. I wanted to take a moment here to list some of the fake antivirus and spyware removals that you should stay away from or you’ll find your computer infected even worse.
How Does the Fake Antivirus Detection Software Work?
Fake antivirus removal software packages advertise and promote themselves as product that will help you remove malicious software from your computer. The moment you download and install one, you are really in big trouble. You have now been infected by one of the most malicious worst Trojans you could have on your computer. The moment it is installed, pop-up windows appear informing you of horrible infections. They prompt you to click on a link so you can download the full version of the antivirus software to thoroughly clean your computer. Another version presents itself as a legitimate antivirus software and fakes a “full system scan,” which results in a long list of horrible viruses and other assorted nasty-looking infections. When you click on “remove,” you are informed that you only have the trial version and that you need to buy the full version to remove the viruses. Few people realize that the scan results themselves are fake. Most of these are simply a ploy to obtain personal information – especially your credit card information.
The Top Antivirus and Spyware Removals to Avoid Like the Plague
At the end of 2008, ComputerWorld reported on how the latest version of Microsoft’s Malicious Software Removal Tool discovered and removed “Antivirus 2009,” from a reported 394,000 computers in just the initial nine days after it was released. What this reveals is that the scammers who write this fake software are successfully taking advantage of the fear computer users have regarding computer infections, and the lack of most computer user’s computer knowledge. Thousands of people click on links to download fake antivirus software. They essentially voluntarily infect their own computers with a Trojan and other malware and viruses.
The Infamous Antivirus 2009
Antivirus 360, Antivirus 2009, Antivirus 2010, Antivirus 2011 (and probably soon enough Antivirus 2012) are well-known by most IT professionals as malware. You most likely will not find the scammers using legitimate websites to promote these products using their actual names. Scammers are resorting to setting up sites to help people remove Antivirus 2009. They trick you into clicking on the link that downloads and installs the software. Then you find your machine infected with the malicious software.
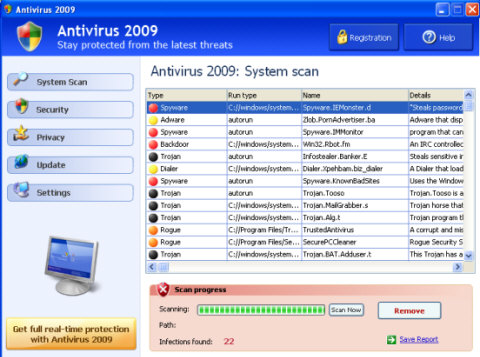
“Removing” the fake viruses from your computer entails signing up (and of course providing your credit card information to pay for) a “full” version of the software. If you fall for this particular trap, at best (if you are lucky) you end up with a charge on your credit card and bogus software. At worst, your credit card is maxed out and you are in for the problems associated with credit card or identity fraud.
Conficker Worm Installs Spyware Protect 2009
Most IT professionals remember the recent Conficker worm fiasco that had them scrambling to patch PCs before they could get infected. An April 10th, 2009 article on CNET reported that investigators discovered a clue behind the motives of the Conficker worm creators – to make money using fake antivirus software. They did so by having the Conficker worm install antivirus software called Spyware Protect 2009 on target computers.
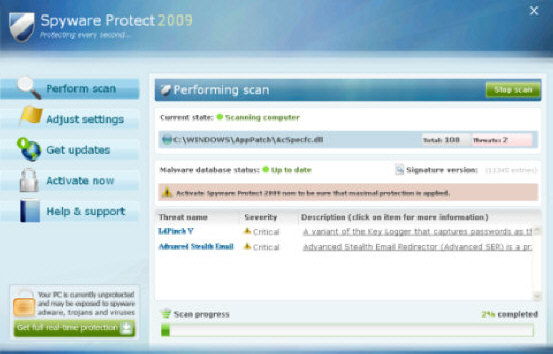
It works essentially the same as the other fake antivirus applications. The software provides users with a list of nasty infections that their computer allegedly has. The only way to remove them is by visiting the website and submitting your credit card information in order to buy the full version. The whole point of the Conficker worm was another fake antivirus scam. If your computer ever displays the window above, you’re likely infected with the Conficker worm.
PC AntiSpy Returns Fake Spyware Results
PC AntiSpy is another application that also returns bogus results. It lists some of the worst known spyware applications as infecting your computer. PC AntiSpy is a bogus spyware-fighting application that is nothing of the sort. Instead of helping you keep your computer clean, this application uses scare tactics to get users to click on a link to pay for a version of PC AntiSpy that can remove the nasty Spyware that supposedly exists on the computer.
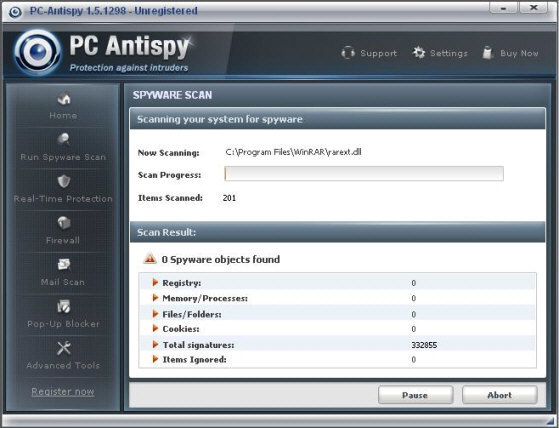
Some of these software packages appear pretty authoritative and legit. Unfortunately the only real functionality they have is acting as a Trojan horse – letting other nasty software and malware infect your system. Like many other fake applications, a multitude of helpful websites and forums post instructions on how to remove it. Scammers continue to become sneakier — they start their own “how to” web pages in order to target people who are already infected and looking for help.
WinDefender – The Copycat Class of Fake Antivirus and Spyware Removals
A significant group of bogus antivirus applications are those that attempt to copy the names of legitimate, well known applications. SpyWareBot and TheSpyBot are both examples that attempt to copy SpyBot Search and Destroy. These applications depend upon computer users who aren’t technically savvy and aren’t sure exactly what the legitimate software is called. WinDefender is another example which attempts to mimic Windows Defender.
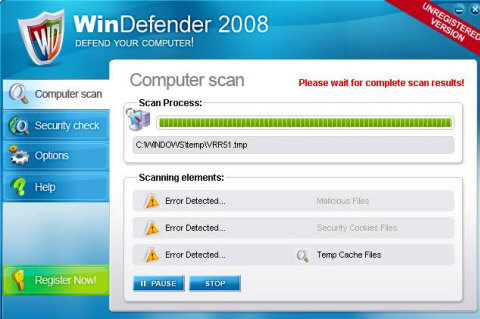
These applications are very successful in fooling people. That’s because so many people see them as similar to the genuine application’s names and look they are mimicking. The most important rule of thumb to follow when you’re looking for good antivirus or anti-spyware software is to only shop at websites that you know are reputable. Whenever an antivirus ad automatically pops up unexpectedly on your computer screen, under no circumstances should you ever click the link to “run a scan.”
Bottom Line – Use Caution and Common Sense
We have used Symantec and Norton AntiVirus products for many years and normally recommend them to others. We often have machines sent our way for virus removal and fewer of those are running Norton or Symantec Antivirus products than any other antivirus software. Nothing says that you must use only Norton or Symantec for your antivirus needs, but if you’re going to branch out and try other software companies, it’s important that you understand the legitimacy and integrity of the company you choose. The examples above are only four of the hundreds of fake antivirus and anti-spyware applications out there – and their names change just as fast as people can figure out that they’re fake.


